technology

The Tor Project is a free network run by volunteers that hides users locations and usage from surveillance and traffic analysis. Essentially, it provides online anonymity to anybody who wants it. Tor users can send email and instant message, surf websites and post content online without anyone knowing who or where they are. (…)
It’s no surprise then that the Great Firewall of China, as it is called, actively blocks access to the Tor network. So an interesting question is how this censorship works and how it might be circumvented.
Today, Philipp Winter and Stefan Lindskog at Karlstad University in Sweden provide an answer.
{ The Physics arXiv Blog | Continue reading }
Anonymous has hacked hundreds of Chinese government websites. Some sites were just defaced, but others have had administrator accounts, phone numbers, and e-mail addresses leaked.
{ ZDNet | Continue reading }
asia, technology | April 5th, 2012 11:00 am
Imagine that you have a big box of sand in which you bury a tiny model of a footstool. A few seconds later, you reach into the box and pull out a full-size footstool: The sand has assembled itself into a large-scale replica of the model.
That may sound like a scene from a Harry Potter novel, but it’s the vision animating a research project at the Distributed Robotics Laboratory (DRL) at MIT’s Computer Science and Artificial Intelligence Laboratory.
At the IEEE International Conference on Robotics and Automation in May — the world’s premier robotics conference — DRL researchers will present a paper describing algorithms that could enable such “smart sand.”
{ MIT News | Continue reading }
science, technology | April 4th, 2012 10:53 am

One quick story: I was a venture capitalist in 2001. A company, Oingo, which later became Applied Semantics, had a technique for how search engines could make money by having people bid for ads. My partner at the firm said, “we can probably pick up half this company for cheap. They are running out of money.” It was during the Internet bust.
“Are you kidding me, “ I said. “they are in the search engine business. That’s totally dead.” And I went back to playing the Defender machine that was in my office. That I would play all day long even while companies waited in the conference room.
A year later they were bought by Google for 1% of Google. Our half would’ve now been worth hundreds of millions if we had invested. I was the worst venture capitalist ever. They had changed their name from Oingo to Applied Semantics to what became within Google…AdWords and AdSense, which has been 97% of Google’s revenues since 2001. 97%. $67 billion dollars. (…)
Ken Lang buys his patents back from Lycos for almost nothing. He starts a company: I/P Engine. Two weeks ago he announced he was merging his company with a public company, Vringo (Nasdaq: VRNG). Because it’s Ken, I buy the stock although will buy more after this article is out and readers read this.
The company sues Google for a big percentage of those $67 billion in revenues plus future revenues. The claim: Google has willfully infringed on Vringo – I/P’s patents for sorting ads based on click-throughs.
{ James Altucher/TechCrunch | Continue reading }
economics, google, law | April 3rd, 2012 7:26 am

Computers dominate how we live, work and think. For some, the technology is a boon and promises even better things to come. But others warn that there could be bizarre consequences and that humans may be on the losing end of progress. (…)
“Economic progress ultimately signifies the ability to produce things at a lower financial cost and with less labor than in the past,” says Polish sociologist Zygmunt Bauman. As a result, he says, increasing effectiveness goes hand in hand with rising unemployment, and the unemployed merely become “human waste.”
Likewise, (…) Erik Brynjolfsson and Andrew McAfee, both scholars at the MIT, argue that, for the first time in its history, technological progress is creating more jobs for computers than for people.
{ Spiegel | Continue reading }
unrelated { Competition among memes in a world with limited attention }
economics, ideas, technology, uh oh | April 3rd, 2012 7:25 am

Sometime last year computers at the U.S. Social Security Administration were hacked and the identities of millions of Americans were compromised. What, you didn’t hear about that? Nobody did.
The extent of damage is only just now coming to light in the form of millions of false 2011 income tax returns filed in the names of people currently receiving Social Security benefits.
{ Robert X. Cringely | Continue reading }
U.S., economics, scams and heists, technology | April 2nd, 2012 1:02 pm

{ Only 500 people have been to space, only three people have been to the bottom of the ocean, but no one has ever attempted to journey to the core of an active volcano. Until now. Using patented carbon-carbon materials pioneered for deep space exploration, Virgin is proud to announce a revolutionary new vehicle, VVS1, which will be capable of plunging three people into the molten lava core of an active volcano. | Virgin | Continue reading | Thanks Tim }
elements, technology, transportation | April 2nd, 2012 1:00 pm

Sixty-five million years ago, a Manhattan-size meteorite traveling through space at about 11 kilometers per second punched through the sky before hitting the ground near what is now Mexico’s Yucatán Peninsula. The energy released by the impact poured into the atmosphere, heating Earth’s surface. Then the dust lofted by this impact blocked out the sun, bringing years of wintry conditions everywhere, wiping out many terrestrial species, including the nonfeathered dinosaurs. Birds and mammals thus owe their ascendancy to the intersection of two orbits: that of Earth and that of a devastating visitor from deep space. (…)
In December 2004, scientists at NASA and the Jet Propulsion Laboratory (JPL), in Pasadena, Calif., estimated there was a nearly 3 percent chance that a 30-billion-kilogram rock called 99942 Apophis would slam into Earth in 2029, releasing the energy equivalent of 500 million tons of TNT. That’s enough to level small countries or raise tsunamis that could wash away coastal cities on several continents. More recent calculations have lowered the odds of a 2029 impact to about 1 in 250 000. This time around, Apophis will probably miss us—but only by 30 000 km, less than one-tenth of the distance to the moon. (…)
We considered several strategies. The most dramatic—and the favorite of Hollywood special-effects experts—is the nuclear option. Just load up the rocket with a bunch of thermonuclear bombs, aim carefully, and light the fuse when the spacecraft approaches the target. What could be simpler? The blast would blow off enough material to alter the trajectory of the body, nudging it into an orbit that wouldn’t intersect Earth.
But what if the target is brittle? The object might then fragment, and instead of one large body targeting Earth, there could be several rocks—now highly radioactive—headed our way.
{ IEEE Spectrum | Continue reading }
painting { Nicola Verlato }
incidents, space, technology | April 2nd, 2012 5:15 am

When Facebook goes public this year, it will raise at least $5 billion, making it the biggest Internet IPO the world has ever seen. The day it debuts on the stock exchange, Facebook will be worth more than General Motors, the New York Times Company, and Sprint Nextel combined. (…)
For roughly 65 years—say, from 1933 to 1998—the initial public offering was the engine of American capitalism. Entrepreneurs sold shares to investors and used the proceeds to build their young companies or invest in the future. After their IPOs, for instance, Apple and Microsoft had the necessary funds to develop the Macintosh and Windows. The stock market has been the most efficient and effective method of allocating capital that the world has ever seen.
That was a useful function, but it’s one that IPOs no longer serve. Going public is more difficult than it used to be—Sarbanes-Oxley regulations have made filing much more difficult, and today’s investors tend to shy away from Internet companies that don’t have a proven track record of steady profitability. That has created a catch-22: By the time a company can go public, it no longer needs the cash. Take Google. It had already been profitable for three years before raising $1.2 billion in its 2004 public offering. And Google never spent the money it raised that year. Instead, it put the cash straight into the bank, where the funds have been sitting ever since. Today, Google’s cash pile has grown to more than $44 billion.
{ Wired | Continue reading }
photo { Femke Hiemstra }
economics, technology | March 30th, 2012 1:53 pm

A new approach to fMRI scanning offers a three-dimensional look at brain activation.
fMRI is already a 3D technique, of course, but in the case of the cerebral cortex - which is what the great majority of neuroscientists are most interested in - the 3D data are effectively just 2D images folded up in space. (…)
In a new paper, Minnesota neuroscientists Olman et al say that they’ve given fMRI a third dimension.
{ Neuroskeptic | Continue reading }
related { functional MRI (fMRI) is an MRI procedure that measures brain activity by detecting associated changes in blood flow. }
health, neurosciences, technology | March 30th, 2012 1:53 pm

It’s been a long time coming, but last night it happened: one of the greatest hackers of the 20th Century (or was it just his doppelganger?) went up against Anonymous, greatest hacktivist collective of the 21st Century. (…)
Mitnick was a legendary hacker at the dawn of the Internet and before. Convicted of wire fraud, computer fraud, and illegally intercepting a wire communication, he served nearly four years in prison. (…)
Tuesday night, he, or someone impersonating him, decided to play with Anonymous.
{ The Daily Dot | Continue reading }
photo { Daniel Ribar }
technology | March 29th, 2012 12:43 pm
showbiz, technology | March 28th, 2012 8:47 am

Who made and launched Stuxnet in the first place? Richard Clarke tells me he knows the answer.
Clarke, who served three presidents as counterterrorism czar, now operates a cybersecurity consultancy called Good Harbor. (…) We have virtually no defense against the cyberattacks that he says are targeting us now, and will be in the future. (…)
“I think it’s pretty clear that the United States government did the Stuxnet attack,” he said calmly.
{ Smithsonian | Continue reading }
previously, Stuxnet { The out-of-controller | I don’t sleep. I wait. }
illustration { Jonathan Koshi }
mystery and paranormal, technology | March 28th, 2012 8:40 am
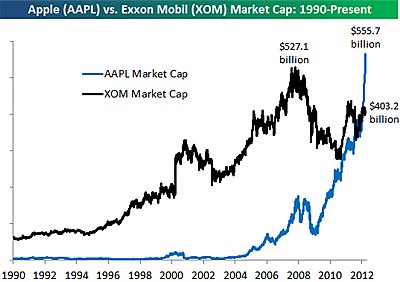
The speculation of what Apple is going to do with all their cash has long been a favorite topic in the tech and financial press. (…) What’s the point of having all that money if you’re not going to spend it?
That thinking is what we saw when Apple recently announced their cash plans. (..) “Saddened by Apple’s plan for a huge dividend. Apparently, they have nothing truly capital-intensive in the product pipeline.” (…)
Even after issuing dividends and repurchasing shares, Apple’s cash reserves will likely grow this year. They added more than $35 billion in cash and equivalents last year alone. There’s nothing “capital-intensive” that they can’t do, short of opening an Apple Store on the moon. (…)
The idea floating around before Apple’s Monday announcement that they would be buying a company like Foxconn or building factories of their own seems to make sense, since Apple is one of the more vertically integrated consumer electronics companies in the world. And they are, after all, notorious for both control and quality. But they’ve managed to lead the industry on the latter without owning a significant portion of their supply chain. (…)
Apple has this enormous negotiating power, and they use it, I am told by our sources, very aggressively to come in and basically say, “Show us your entire cost structure, every single part of what you pay and what you… and we are going to give you a razor-thin profit margin that you’re allowed to keep.
In other words: Why buy the cow?
Apple also, more importantly, finances the factories by loaning them cash and buying significant amounts of components in advance. This “Bank of Apple” strategy further establishes control over the factories, locks out competition and seems to be why competitors can’t seem to match Apple’s cost structure for products like the iPad. (…)
This brings us to those who think Apple has run out of ideas on what to do with their cash. The fevered result of this are the acquisition talks — hence the recently oft-mentioned and largely nonsensical suggestion that Apple should buy a company like Twitter. But Apple’s approach to acquisitions has always been extremely conservative, especially compared to their brethren. Since 2010 Apple’s bought a grand total of nine companies. In that same period Google has bought 52.
{ TechCrunch | Continue reading | Thanks Glenn }
related { The FBI made public a background investigation of Steve Jobs in 1991, when he was being considered by the George H. W. Bush administration for a spot on the President’s Export Council. }
economics, technology | March 28th, 2012 5:50 am

Facebook has trademarks on its name and many variations of it—including the letter “F.” The company is expanding its claim over the word “book.”
{ Ars Technica | Continue reading }
also { Facebook says it may sue employers who demand job applicants’ passwords }
social networks | March 26th, 2012 1:00 pm

Researchers have established a direct link between the number of friends you have on Facebook and the degree to which you are a “socially disruptive” narcissist, confirming the conclusions of many social media skeptics.
People who score highly on the Narcissistic Personality Inventory questionnaire had more friends on Facebook, tagged themselves more often and updated their newsfeeds more regularly.
The research comes amid increasing evidence that young people are becoming increasingly narcissistic, and obsessed with self-image and shallow friendships.
A number of previous studies have linked narcissism with Facebook use, but this is some of the first evidence of a direct relationship between Facebook friends and the most “toxic” elements of narcissistic personality disorder.
{ Guardian | Continue reading }
photo { Leo Berne }
quote { Hamilton Nolan/Gawker }
gross, ideas, psychology, social networks, technology | March 25th, 2012 11:18 am

The problem with the web is that it largely began as a world separate from meatspace. Today, most people use their real names, but this wasn’t always the case. When I started going online in the mid-90s, no one even knew my gender. I preferred that, not because I was hiding, but because I feel very strongly that I should be judged by my thoughts, not who people assume I am by seeing I am a woman, by attaching a handful of preconceived notions to what I am saying because they see my photo and think I’m too young or too old or attractive or unattractive. (…)
There is nothing wrong with wishing that it were possible to compartmentalize your digital conversations in the same way you do your meatspace exchanges. Unfortunately for us, this is not the direction the web is going, which is why pseudonymous accounts and the networks who accept them are so very, very important.
{ AV Flox | Continue reading }
image { Mark Gmehling }
experience, ideas, technology | March 23rd, 2012 11:48 am

A Star Trek-style cloaking technique allows people to spy on your Facebook account in a way that is difficult to spot and even harder to stop, say computer scientists.
{ The Physics arXiv Blog | Continue reading }
illustration { Grant Orchard }
spy & security, technology | March 22nd, 2012 3:45 pm
technology, visual design | March 22nd, 2012 7:30 am

Researchers at Yale University have developed a new way of seeing inside solid objects, including animal bones and tissues, potentially opening a vast array of dense materials to a new type of detailed internal inspection.
The technique, a novel kind of magnetic resonance imaging (MRI), creates three-dimensional images of hard and soft solids based on signals emitted by their phosphorus content.
Traditional MRI produces an image by manipulating an object’s hydrogen atoms with powerful magnets and bursts of radio waves. The atoms absorb, then emit the radio wave energy, revealing their precise location. A computer translates the radio wave signals into images. Standard MRI is a powerful tool for examining water-rich materials, such as anatomical organs, because they contain a lot of hydrogen. But it is hard to use on comparatively water-poor solids, such as bone.
The Yale team’s method targets phosphorus atoms rather than hydrogen atoms, and applies a more complicated sequence of radio wave pulses.
{ Yale News | Continue reading }
artwork { Trevor Brown, Teddy Bear Operation, 2008 }
science, technology | March 19th, 2012 5:19 pm

This has led researchers to ask the questions: How can we get mobile users to break out of their patterns, visit less frequented areas, and collect the data we need?
Researchers can’t force mobile users to behave in a certain way, but researchers at Northwestern University have found that they may be able to nudge them in the right direction by using incentives that are already part of their regular mobile routine.
“We can rely on good luck to get the data that we need,” Bustamante said, “or we can ‘soft control’ users with gaming or social network incentives to drive them where we want them.”
{ McCormick School of Engineering and Applied Science | Continue reading }
related { What Privacy Advocates Don’t Get About Data Tracking on the Web }
related { Google regularly receives requests from government agencies and courts around the world to remove content from our services and hand over user data | Who Does Facebook Think You Are Searching For? | Thanks Samantha! }
horror, spy & security, technology | March 16th, 2012 6:37 pm