technology
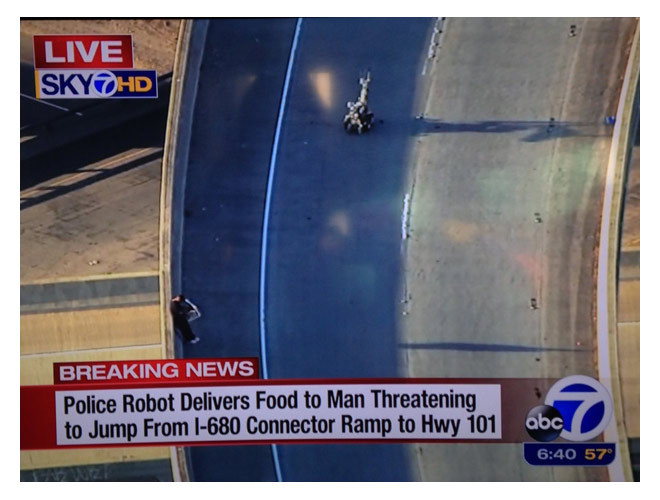
So, some asshole stole my snapshot, put it on reddit (which I didn’t know).
Last night, I posted my pic on reddit.
Now – I found out I got banned and accused of “stealing my own pic.”
Fuck the state of ‘creativity’ and ‘originality’ today. Fuck it.
Let the world implode inside of its own self-licking asshole.
Yes, these silly things mean something to people who actually CREATE anything. […]
No, it’s not yours to fucking ‘remix.’
No, it’s not ’shared’, to be owned by all – even if it’s free.
{ Tim Geoghegan on Facebook }
experience, social networks | July 7th, 2016 9:32 am

Two hedge fund “quants” have come up with an algorithm that diagnoses heart disease from MRI images, beating nearly 1,000 other teams in one of the most ambitious competitions in artificial intelligence.
{ Financial Times | Continue reading }
Qi Liu and Tencia Lee, hedge fund analysts and self-described “quants,” didn’t know each other before they won the competition, beating out more than 1,390 algorithms. They met each other in a forum on the Kaggle site, where the competition was hosted over a three-month period.
{ WSJ | Continue reading }
health, technology, traders | June 24th, 2016 7:41 am

Facebook could be listening in on people’s conversations all of the time, an expert has claimed. The app might be using people’s phones to gather data on what they are talking about.
Professor Burns has said that the tool appears to be using the audio it gathers not simply to help out users, but might be doing so to listen in to discussions and serve them with relevant advertising. She says that to test the feature, she discussed certain topics around the phone and then found that the site appeared to show relevant ads.
Facebook says that its app does listen to what’s happening around it, but only as a way of seeing what people are listening to or watching and suggesting that they post about it.
{ Independent | Continue reading }
unrelated { How Facebook is Stealing Billions of Views }
photo { Marcus Ohlsson }
social networks, spy & security | June 2nd, 2016 10:23 am

An Israeli start-up says it can take one look at a person’s face and realize character traits that are undetectable to the human eye.
Faception said it’s already signed a contract with a homeland security agency to help identify terrorists. The company said its technology also can be used to identify everything from great poker players to extroverts, pedophiles, geniuses and white collar-criminals. […]
Faception recently showed off its technology at a poker tournament organized by a start-up that shares investors with Faception. […] Two of those four were among the event’s three finalists. To make its prediction Faception analyzed photos of the 50 players against a Faception database of professional poker players.
{ Washington Post | Continue reading }
faces, technology | May 27th, 2016 3:10 pm

We present a case with excessive Internet use, with a particular focus on phenomenology and psychiatric comorbidities. Fifteen-year-old girl with childhood onset attention deficit disorder, obsessive-compulsive disorder, adolescent onset trichotillomania, and disturbed family environment presented with excessive Facebook use. Main online activity was creating profiles in names of mainstream fictional characters and assuming their identity (background, linguistic attributes, etc.).
{ Journal of Behavioral Addictions | Continue reading }
art { thedatadrive.com }
related { After learning to identify with someone else’s face, do people think their appearance has changed? }
unrelated { Punk Parents Blame Child’s Terrible Taste in Music on Vaccinations | Thanks GG }
psychology, social networks | May 13th, 2016 12:10 pm
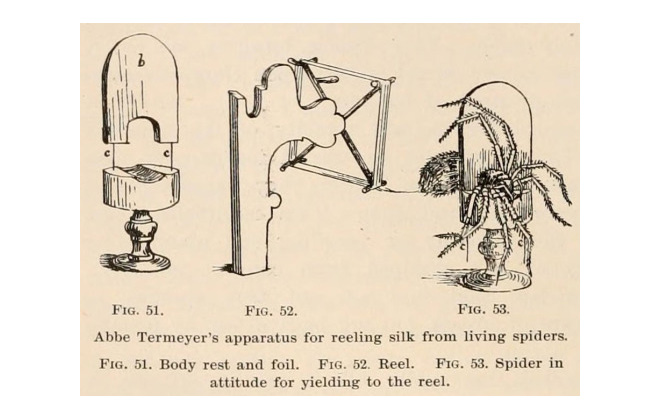
The mantra of Wall St hedge funds was once “only the strongest will survive.” It may now have to change to “the geeks will inherit the earth.”
Hedge fund “quants” who use computer systems to trade financial markets earned more money than some of the industry’s most famous stockpickers, who posted large losses in 2015.
The most prominent among the quants was string theory expert and former code breaker James Simons of Renaissance Technologies, who earned $1.7bn, putting him in joint first place.
He was joined in the top 10 earners by former Columbia University computer science professor David Shaw of DE Shaw who made $750m and John Overdeck and David Siegel of Two Sigma who made $500m each.
Their success came in stark contrast to some of the biggest names on Wall Street who rely on human investment judgment rather than lines of computer code.
{ FT | Continue reading }
quote { Cabinet magazine | full story }
technology, traders | May 10th, 2016 3:13 pm

Please notice how the Director of the NSA, unlike the vociferous FBI director, has been relatively silent. With a budget on the order of $10 billion at its disposal the NSA almost certainly has something equivalent to what the courts have asked Apple to create. The NSA probably doesn’t want to give its bypass tool to the FBI and blow its operational advantage.
{ Counterpunch | Continue reading }
spy & security, technology | February 22nd, 2016 1:59 pm

They’re like, “The internet is public.” A lot of things are public, but it doesn’t mean they’re for you. For instance, you can walk down the street and you can look into all of your neighbors’ windows should they have chanced not to draw the curtains. If you really lean in, you can listen to all kinds of conversations that are too quiet for you to just overhear. You can do all kinds of things in public that you should not do. Are you walking down the street, interrupting random twosomes or threesomes of people to add your two fucking sentences? You’re not, so why are you on my Twitter? Why are you talking to me?
{ Sarah Nicole Prickett / Mask | Continue reading }
photo { Leah Schrager }
social networks | December 7th, 2015 3:38 pm

Experts say fakes have become one of the most vexing problems in the art market. […]
Two years ago, the center, known for its work in bioengineering, encryption and nanotechnology, set about developing a way to infuse paintings, sculptures and other artworks with complex molecules of DNA created in the lab. […]
The new approach, in its formative stage, would implant synthetic DNA, not the personal DNA of the artists, because of privacy issues and because a person’s DNA could conceivably be stolen and embedded, thus undermining the authority of such a marking protocol.
The developers said the bioengineered DNA would be unique to each item and provide an encrypted link between the art and a database that would hold the consensus of authoritative information about the work. The DNA details could be read by a scanner available to anyone in the art industry wanting to verify an object.
{ NY Times | Continue reading }
installation { Yayoi Kusama, The obliteration room, 2002-present }
art, genes, technology | October 22nd, 2015 11:40 am

Artificial-intelligence researchers have long struggled to make computers perform a task that is simple for humans: picking out one person’s speech when multiple people nearby are talking simultaneously.
It is called the ‘cocktail-party problem’. Typical approaches to solving it have either involved systems with multiple microphones, which distinguish speakers based on their position in a room, or complex artificial-intelligence algorithms that try to separate different voices on a recording.
But the latest invention is a simple 3D-printed device that can pinpoint the origin of a sound without the need for any sophisticated electronics.
{ Nature | Continue reading }
photos { 1 | 2. Yo-landi Visser photographed by Pierre Debusschere }
3D printing, noise and signals | August 18th, 2015 9:00 am

By definition, exponential growth means the thing that comes next will be equal in importance to everything that came before. […]
this exponential growth has given us terrible habits. One of them is to discount the present.
{ Idle Worlds | Continue reading }
ideas, technology | July 22nd, 2015 2:09 am

An experimental algorithm out of Facebook’s artificial intelligence lab can recognise people in photographs even when it can’t see their faces. Instead it looks for other unique characteristics like your hairdo, clothing, body shape and pose. […]
The final algorithm was able to recognise individual people’s identities with 83 per cent accuracy.
{ NewScientist | Continue reading }
California-based company Face First is rolling out a system for retailers that it says will “boost sales by recognising high-value customers each time they shop” and send “alerts when known litigious individuals enter any of your locations.”
“What facial recognition allows is a world without anonymity,” says Bedoya. “You walk into a car dealership and the salesman knows your name and how much you make.”
Another company, called Churchix is marketing facial recognition systems for churches. Once the faces of a church’s membership have been added to a database, the system tracks their attendance automatically. It also claims to be able to discern demographic data about the entire congregation, including age and gender.
{ NewScientist | Continue reading }
photo { Aaron McElroy }
faces, technology | June 23rd, 2015 1:29 pm
The future is always stranger than we expect: mobile phones and the Internet, not flying cars. […]
“We’re not funding Mother Teresa. We’re funding imperial, will-to-power people who want to crush their competition. Companies can only have a big impact on the world if they get big.” […]
The dirty secret of the trade is that the bottom three-quarters of venture firms didn’t beat the Nasdaq for the past five years. […] The truth is that most V.C.s subsist entirely on fees, which they compound by raising a new fund every three years. Returns are kept hidden by nondisclosure agreements, and so V.C.s routinely overstate them, both to encourage investment and to attract entrepreneurs. […]
“We live in a financial age, not a technological age.”
{ New Yorker | Continue reading }
economics, technology | May 12th, 2015 1:04 am

Participants were 152 students (88 women, 64 men; average age 19.7) at a “mid-sized university in the northeastern US.” […]
Texting during class was not acceptable, but 84.7% had done this. Texting in the shower is unacceptable and 34% have done this. Texting during the Pledge of Allegiance is unacceptable and 11.3% have done it. Texting while having sex is unacceptable and 7.4% have done it. Talking to a friend and texting another at the same time is unacceptable and between 79% and 84% have done it. Texting one person in whom you are romantically interested while on a date with someone else is unacceptable and 21.5% have done it. Breaking up by text is unacceptable and 26% have done it. Sending text messages while at a funeral is unacceptable and 10.1% have done it. Texting during a job interview is unacceptable and 2.7% have done it. Fighting with some via text is unacceptable and 66% have done it. Sexting is unacceptable and 42% have done it.
{ The Jury Room | Continue reading }
photo { Danny Lyon, New Year’s Eve on the subway, 1966 }
unrelated { Kids can’t tell the difference between journalism and advertising }
kids, technology | April 24th, 2015 1:34 pm
robots & ai | April 24th, 2015 7:29 am

Snapchat, the photo-messaging app raising cash at a $15 billion valuation, probably isn’t actually worth more than Clorox or Campbell Soup. So where did investors come up with that enormous headline number?
Here’s the secret to how Silicon Valley calculates the value of its hottest companies: The numbers are sort of made-up. For the most mature startups, investors agree to grant higher valuations, which help the companies with recruitment and building credibility, in exchange for guarantees that they’ll get their money back first if the company goes public or sells. They can also negotiate to receive additional free shares if a subsequent round’s valuation is less favorable. Interviews with more than a dozen founders, venture capitalists, and the attorneys who draw up investment contracts reveal the most common financial provisions used in private-market technology deals today. […]
Billion-dollar companies join a club of “unicorns,” a term used to explain how rare they are. But there are more than 50 of them now. There’s a new buzzword, “decacorn,” for those over $10 billion, which includes Airbnb, Dropbox, Pinterest, Snapchat, and Uber. It’s a made-up word based on a creature that doesn’t exist.
{ Bloomberg | Continue reading }
economics, social networks, technology | March 17th, 2015 3:59 pm
The ’sex selfie stick’ lets you FaceTime the inside of a vagina
The device offers the unprecedented opportunity to be on the phone with someone’s genitals.
{ Independent | Continue reading }
sex-oriented, technology | March 5th, 2015 3:34 pm

Google started testing their cars on public roads back in 2009, long before any regulations were even dreamed of. An examination of the California Vehicle Code indicated there was nothing in there prohibiting testing.
For testing purposes, Google has a trained safety driver sitting behind the wheel, ready to take it at any moment. Any attempt to take the wheel or use the pedals disables the automatic systems and the safety driver is in control. The safety drivers took special driving safety courses and were instructed to take control if they have any doubt about safe operation. For example, if a vehicle is not braking as expected when approaching a cross walk, take the controls immediately, do not wait to see if it will detect the pedestrians and stop.
The safety drivers are accompanied by a second person in the passenger seat. Known as the software operator, this person monitors diagnostic screens showing what the system is perceiving and planning, and tells the safety driver if something appeared to be going wrong. The software operator is also an extra set of eyes on the road from time to time.
Many other developers have taken this approach, and some of the regulations written have coded something similar to it into law.
This style of testing makes sense if you consider how we train teen-agers to drive. We allow them to get behind the wheel with almost no skill at all, and a driving instructor sits in the passenger seat. While not required, professional driving instructors tend to have their own brake pedal, and know how and when to grab the wheel if need be. They let the student learn and make minor mistakes, and correct the major ones.
The law doesn’t require that, of course. After taking a simple written test, a teen is allowed to drive with a learner’s permit as long as almost any licenced adult is in the car with them. While it varies from country to country, we let these young drivers get full solo licences after only a fairly simple written test and a short road test which covers only a tiny fraction of situations we will encounter on the road. They then get their paperwork and become the most dangerous drivers on the road.
In contrast, robocar testing procedures have been much more strict, with more oversight by highly trained supervisors. With regulations, there have been requirements for high insurance bonds and special permits to go even further. Both software systems and teens will make mistakes, but the reality is the teens are more dangerous.
{ Brad Templeton | Continue reading }
related { Will You Need a New License to Operate a Self-Driving Car? }
google, motorpsycho, robots & ai | March 5th, 2015 10:02 am

Facebook will soon be able to ID you in any photo
The intention is not to invade the privacy of Facebook’s more than 1.3 billion active users, insists Yann LeCun, a computer scientist at New York University in New York City who directs Facebook’s artificial intelligence research, but rather to protect it. Once DeepFace identifies your face in one of the 400 million new photos that users upload every day, “you will get an alert from Facebook telling you that you appear in the picture,” he explains. “You can then choose to blur out your face from the picture to protect your privacy.” Many people, however, are troubled by the prospect of being identified at all—especially in strangers’ photographs. Facebook is already using the system, although its face-tagging system only reveals to you the identities of your “friends.”
{ Science | Continue reading }
related { Bust detection algorithm }
photo { Rachel Roze }
Linguistics, faces, social networks | February 7th, 2015 3:03 pm